Today is the modern age of information where information travels in every direction in air without depending on wires. Information is getting transmitted over wireless networks. You will probably find everywhere some wifi hotspot either you are in the office or you go to some coffee shop. So, what if you don’t have an internet connection and wanted to connect to some secured wifi network.. The problem is most of the wifi hotspots are secured by the password key usually by WPA2 encryption. In order to get connected, you need to have password key. In this step by step tutorial, I will show how to hack wifi wpa and wpa2 encrypted password to connect to these secured networks.
- Injection Supported Wifi Card (Encryption supported. i.e: Alfa AWUS036H)
- Kali Linux OS
- Wordlist of Passwords (Google it to download)
Related: Best Remote Administration Tools
Step by Step Instructions
- Download Kali Linux from their official website and install it.
- Once it’s installed and active, open up a terminal in the Kali Linux and put the Wifi card in Monitor mode by typing these commands. ‘ifconfig wlan0 down‘ , ‘iwconfig wlan0 mode monitor‘and ‘ifconfig wlan0 up‘.
- As your card shows Mode Monitor as shown in below screenshot. Run the command ‘airodump-ng wlan0‘ to monitor the networks.
- Now we will write these captured packets in a file by the command as below. You can change the ‘bssid‘ and ‘channel‘ according to the output of step 3. Bssid is the mac address of the wifi network device.
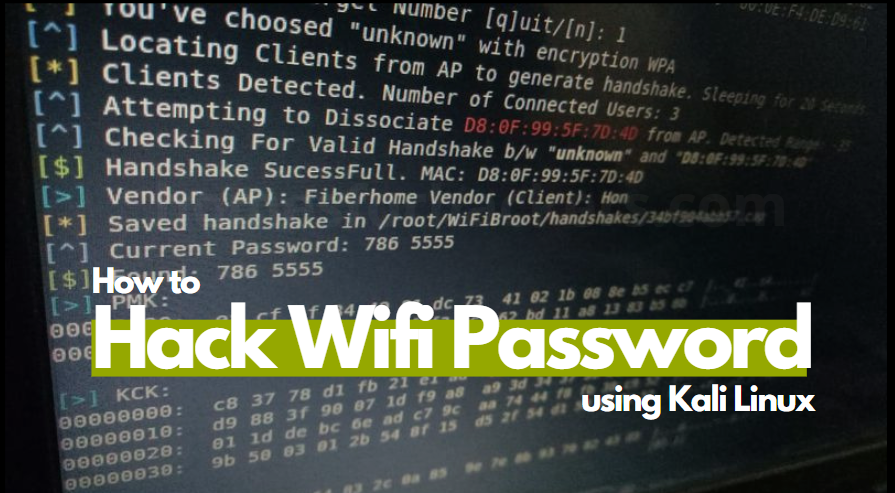
- Now we need to deauthenticate any of the connected device from the wifi network. It’ll capture the handshake packet. As you type the command as in the second terminal, you’ll get handshake packet in top right corner of the terminal like highlighted in the below screenshot.
- Now we have the handshake packet and we have wordlist. So we are good to go for the final command to crack the password and hit enter.
- Booom..!! We got the wifi network key. Password key of the network have been found successfully.
That’s all. Hope it will work for you. If you’re confused in any step on how to hack wifi wpa2 encrypted password, feel free to drop comment below. Happy Cracking..!!